Best Practices for Implementing NIST Password Guidelines, with Special Instructions for Active Directory
PDF) NIST Special Publication 800-114 Revision 1, User's Guide to Telework and Bring Your Own Device (BYOD) Security
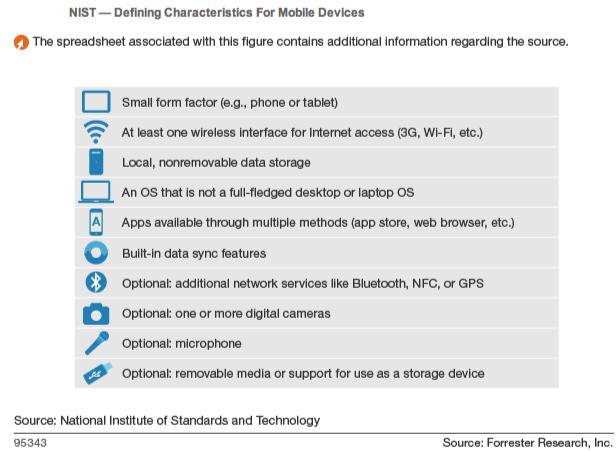
Draft NIST SP 800-124 Rev. 2, Guidelines for Managing the Security of Mobile Devices in the Enterprise






:quality(70)/cloudfront-us-east-1.images.arcpublishing.com/archetype/FKV56FCQAJERXH3NVHVZBCCCS4.jpg)